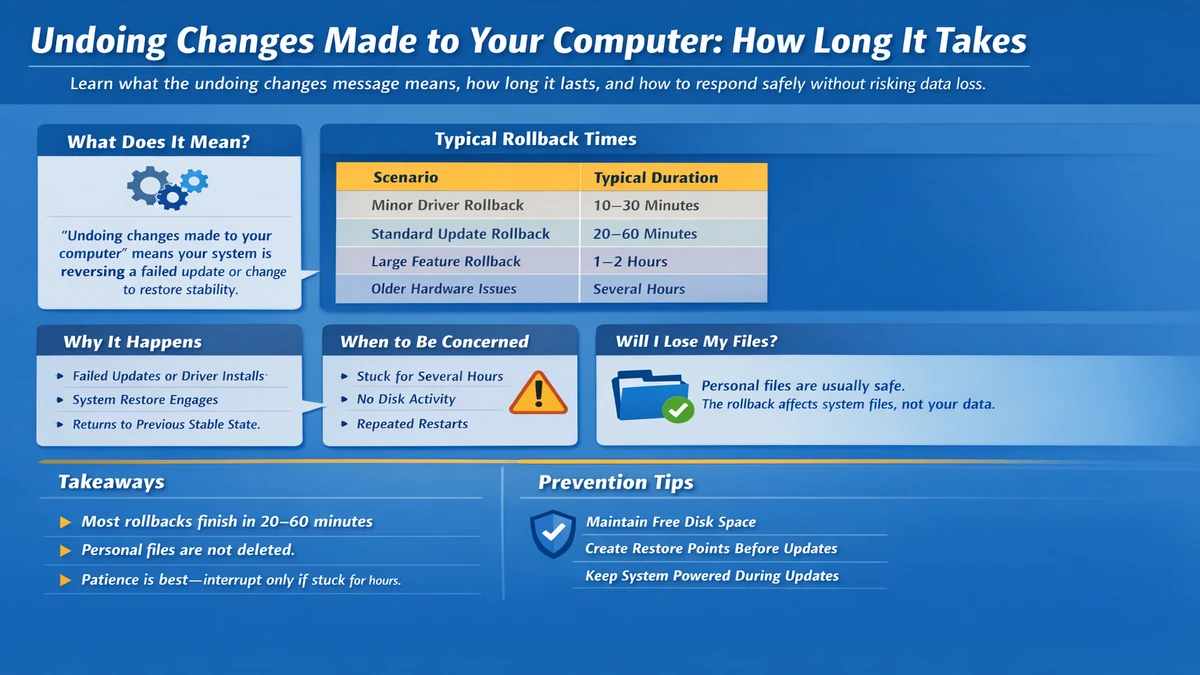
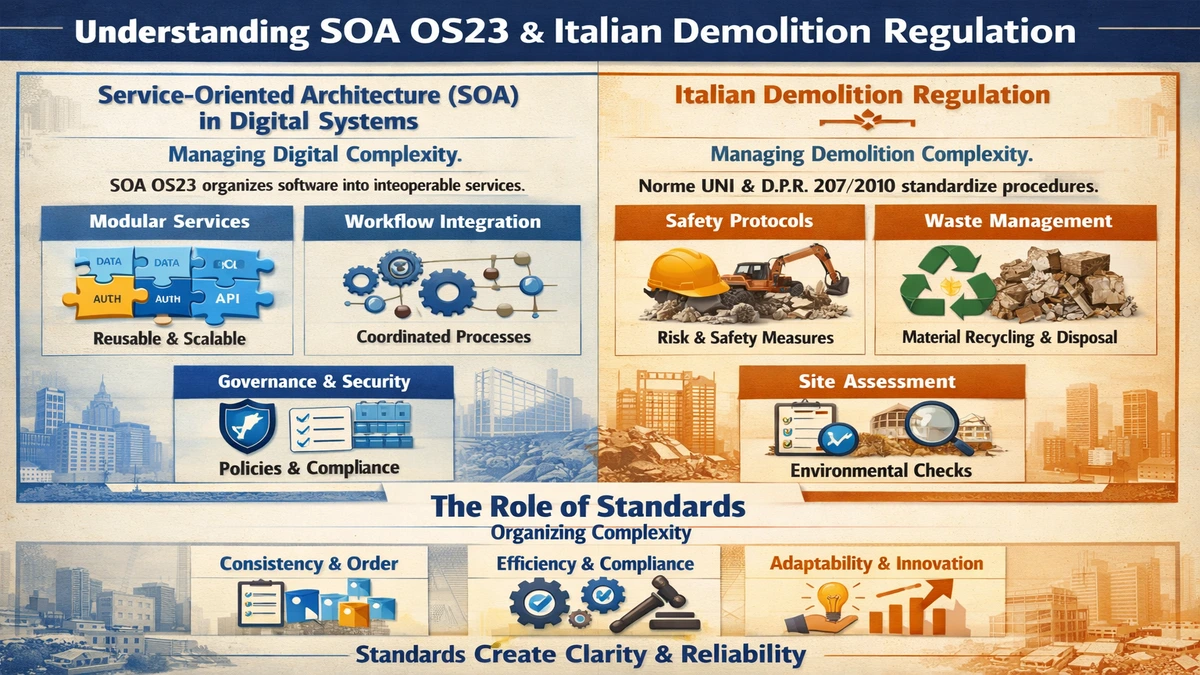
Few things unsettle everyday Android users more quickly than stumbling upon a mysterious path like content://cz.mobilesoft.appblock.fileprovider/cache/blank.html. It appears without warning, often inside a browser’s address bar, a logging tool, or a system dialog, looking nothing like a normal website or file location. For many, the first instinct is concern: is this a virus, a security breach, or evidence of someone accessing private data? Yet the truth is far more routine and far more structural: this URI is a standard Android construct, a direct result of how the operating system isolates applications, protects data, and allows apps to serve local content securely. The search intent behind this topic is straightforward, and it can be answered in the first hundred words: this URI refers to a local placeholder HTML file created by the AppBlock application, delivered through Android’s FileProvider system. It is not a website, not a public Internet address, and not malware. Instead, it is a controlled, sandboxed redirection tool used when AppBlock intercepts an attempt to open blocked content. – content://cz.mobilesoft.appblock.fileprovider/cache/blank.html.
Understanding why such a path appears requires stepping into the architecture of how Android manages data access and how certain applications—particularly ones involved in filtering, blocking, or limiting usage—take advantage of the platform’s secure sharing mechanisms. It also means examining how a seemingly blank page, quietly delivered via a structured URI, plays an outsized role in the user experience. As this report unfolds, it will trace not only how the file exists but why it functions the way it does, what situations cause it to surface, how it fits into broader privacy design choices, and what users can do if they want greater control. Behind the cryptic path sits a surprising amount of thought, engineering intentionality, and privacy-focused design. – content://cz.mobilesoft.appblock.fileprovider/cache/blank.html.
Understanding Android’s Content URI System
At the heart of this discussion is the “content URI,” a format Android created to replace direct file paths. Unlike older mobile systems that exposed filesystem directories freely, Android hides internal app storage behind permissions, sandboxing, and brokered access. A content URI—always beginning with content://—acts as a secure pointer to a file or dataset managed by a specific application. It is not a web URL. It is not accessible through the Internet. It simply describes, in a structured way, a resource held by an app.
Within this system sits the FileProvider, a mechanism that allows apps to safely share certain internal files. Rather than exposing private directories like /data/data/app/cache/, the FileProvider hands out temporary, permission-bound pointers that allow another app—like a browser or a viewer—to display a file without ever learning where the file lives in the actual file system. This is the architecture that makes stored photos shareable through messaging apps and that allows browsers to load local cached pages without compromising privacy.
Apps must declare their FileProvider explicitly, name an authority unique to their package, and define which paths are allowed to be shared. The authority in our case—cz.mobilesoft.appblock.fileprovider—belongs to AppBlock, a productivity and content-blocking utility. The presence of the authority in a URI indicates that AppBlock intentionally provided the file to another component. – content://cz.mobilesoft.appblock.fileprovider/cache/blank.html.
Breaking Down the Path: A Line-by-Line Interpretation
Here is a human-readable breakdown of the path:
| Component | Meaning |
|---|---|
content:// | The operating system’s secure URI scheme for app-managed data. |
cz.mobilesoft.appblock.fileprovider | The authority: AppBlock’s FileProvider component. |
/cache/ | Directory inside AppBlock’s internal storage designated for shared cached files. |
blank.html | A minimal or empty HTML file, usually used as a neutral placeholder. |
Because the file lives in an app-controlled cache directory, it is temporary by design. Cache contents are expected to be recreated, replaced, or deleted regularly. The FileProvider exposes only what the app chooses to share—not everything inside the directory. The path reveals that AppBlock is intentionally handing a file called blank.html to the requesting app, most often the browser. – content://cz.mobilesoft.appblock.fileprovider/cache/blank.html.
Why AppBlock Uses blank.html
AppBlock’s function is simple: restrict access to distracting websites or apps. To achieve this, it must prevent the external content from loading. But blank-page redirection solves several practical and technical concerns:
- Instantaneous Response
A cached HTML file loads faster than a network error page. Showing a clean blank page avoids the visual noise of error messages. - Controlled Experience
A neutral HTML file avoids showing any branding, ads, or unintended content when a site is blocked. - Stability
Browsers and in-app WebViews handle redirections to valid HTML files more reliably than aborted network calls. - Privacy and Efficiency
Because the file is local, no network request is sent to the originally requested website, maintaining privacy.
The blank page is not an accident; it is a deliberate design choice intended to create a smooth blocking experience without using intrusive banners or pop-ups. – content://cz.mobilesoft.appblock.fileprovider/cache/blank.html.
Situations Where Users Encounter the URI
Users most often encounter the mysterious URI in one of the following situations:
- Blocking a Website
When a user tries to open a blocked domain, the browser is instructed—via intent or redirection—to load the blank HTML file. - Debugging or Developer Logging
Software logs may spill content URIs during routing, WebView events, or permissions checks. - Internal Error Handling
If the cached blank file is missing or corrupted, the system may display the path instead of the rendered output. - Third-Party Browsers or Embedded WebViews
Some browsers reveal the literal URI in the address bar, especially lightweight or privacy-focused ones that avoid masking redirects.
In all cases, the URI is local, safe, and part of expected system behavior.
Technical Issues and User-Side Fixes
Even though the design is intentional, issues can arise. These are common patterns and remedies:
| Problem | Likely Cause | Practical Fix |
|---|---|---|
| Blank page appears too often | Aggressive blocking rules or a misconfigured schedule | Review and update AppBlock’s active blocklists |
| “Cannot display file” error | Missing or corrupted blank.html in the cache | Clear AppBlock’s cache or reinstall |
| Repeated permission prompts | Android restricting URI permissions after updates | Grant AppBlock file access permissions |
| Browser freezes on redirect | WebView incompatibility | Update browser or disable AppBlock for that app |
Such problems are not security threats but rather misconfigurations or cache issues.
Expert Observations and Contextual Quotes
Mobile Systems Engineer, Prague:
“Users tend to assume any unfamiliar URI is malicious. In practice, content URIs are the safest elements on the device. They’re strictly governed by the app that owns them.”
Android Security Architect, Berlin:
“One blank HTML file served through a FileProvider tells you more about an app’s respect for privacy than any splash screen. It means the app isn’t sending data to external servers; it’s handling the redirection internally.”
Digital Well-Being Researcher, London:
“The psychological effect of an instant blank page is significant. It breaks the loop of distraction more effectively than warning messages or error banners.”
These perspectives underscore how a small technical artifact fits into broader themes of privacy, design, and human behavior. – content://cz.mobilesoft.appblock.fileprovider/cache/blank.html.
The Privacy Logic Behind Content URIs
Android’s designers built ContentProvider and FileProvider systems for reasons that extend beyond convenience. They embody a philosophy: apps should only be able to see what they are explicitly allowed to see. A content URI ensures:
- No app can browse another app’s files.
- Access expires the moment the hosting app revokes permission.
- Only the file referenced by the URI is exposed, not the surrounding directory.
- The calling app never learns the real filesystem path.
These protections also limit what malicious apps can attempt. Without content URIs, sandboxing would be far weaker, and cross-app data breaches far more common.
A Broader Look at Why Blank Pages Matter
Although blank pages seem simple—even trivial—they play a subtle role in the mobile experience. They are:
- Neutral
They do not provoke emotional responses. - Consistent
Every blocked page looks the same, reinforcing habit-forming boundaries. - Low-Noise
No alerts, flashing icons, or system warnings. - Non-Disruptive
They avoid making users feel scolded by their own devices.
Apps like AppBlock rely on minimalism because the purpose is behavioral, not punitive. – content://cz.mobilesoft.appblock.fileprovider/cache/blank.html.
Comparative Overview of Blocking Approaches
Below is a high-level comparison of blocking techniques and their impacts:
| Blocking Style | Example Behavior | Pros | Cons |
|---|---|---|---|
| Blank HTML Redirection | Shows empty page | Fast, private, clean | Confusing if user doesn’t understand URI |
| Error-Style Blocking | Shows error banner | Clear message | Feels disruptive |
| Pop-up Interruption | Modal dialog | Explicit enforcement | Breaks workflow |
| Network Interception | DNS rewrites | Wide coverage | Less precise, may slow browsing |
AppBlock’s method aligns with the blank-page approach: subtle, unobtrusive, locally processed.
Why This URI Does Not Indicate Malware
It bears repeating: the content URI is not a sign of malware. Several indicators confirm its safety:
- It begins with
content://, nothttp://. - It contains the AppBlock authority, not an unknown domain.
- It points to a
.htmlfile inside a designated cache path. - It relies on an Android-approved file-sharing mechanism.
- It appears only when the app performs a documented function.
Malware rarely uses content URIs because it cannot gain access to other apps’ FileProviders without permission. – content://cz.mobilesoft.appblock.fileprovider/cache/blank.html.
The User Experience: Why It Appears in Browsers
When a browser tries to load a page blocked by AppBlock, the authorization chain unfolds quickly:
- User requests website.
- AppBlock’s rules intercept.
- Browser receives a redirection command.
- Browser opens FileProvider pointer.
- Blank HTML loads instantly.
Some browsers, especially less feature-heavy ones, display the literal URI because they don’t mask internal redirects. This explains why some users see the path prominently while others never notice it.
The Developer’s Perspective
Developers who rely on WebView often encounter this URI during testing. They may see logs like:
- “Loaded URL: content://cz.mobilesoft.appblock.fileprovider/cache/blank.html”
- “Received redirect to local file”
- “Permission check passed: content URI granted”
This is expected behavior. To ensure compatibility, developers usually need to:
- Enable content access in WebView.
- Grant read URI permission for incoming intents.
- Check that FileProvider authorities do not conflict with their own.
These small steps ensure predictable behavior when apps like AppBlock interact with their content. – content://cz.mobilesoft.appblock.fileprovider/cache/blank.html
The Larger Philosophy: Local Is Safer
Modern mobile platforms increasingly prefer local solutions to network-dependent ones. Serving a blank HTML file locally rather than relying on a remote error page ensures:
- No accidental data transmission.
- No network latency.
- No risk of revealing attempted browsing history to external servers.
- A consistent experience regardless of connectivity.
What looks like a tiny file in a cache folder is actually an example of privacy-conscious engineering. – content://cz.mobilesoft.appblock.fileprovider/cache/blank.html.
Takeaways
- The URI is a normal, safe Android content path generated by the AppBlock application.
- It points to a cached blank HTML file used for blocking or redirecting websites.
- Content URIs are part of Android’s secure architecture for sharing internal files.
- A blank HTML approach minimizes distraction and preserves privacy.
- Users can modify or remove the behavior by adjusting AppBlock settings or clearing cache.
- Seeing this URI does not indicate malware.
- The blank file supports stability, speed, and consistent user experience.
Conclusion
The appearance of content://cz.mobilesoft.appblock.fileprovider/cache/blank.html can initially seem perplexing, even ominous. Yet what lies beneath the surface is far from mysterious: it is a window into how Android protects user privacy, how applications enforce boundaries, and how design choices around minimal redirection can profoundly influence user behavior. The blank HTML file, tucked away in AppBlock’s cache, embodies the broader principle of local control—keeping interactions on the device rather than pushing them through the network. Understanding this URI means understanding the quiet architecture that governs modern mobile security: one shaped not by spectacle but by subtle, intentional mechanisms that ensure safety, consistency, and respect for user autonomy. In this way, a single blank HTML file becomes a testament to thoughtful engineering hiding in plain sight.
FAQs
Why does this URI appear in my browser?
Because AppBlock redirected your request to a local blank file when you attempted to access a blocked website.
Is this URI dangerous?
No. It is a secure, local Android file reference created intentionally by AppBlock.
Does this URI indicate someone is monitoring my device?
No. It only reflects AppBlock’s internal redirection system.
Can I stop this from appearing?
Yes. Adjust or disable AppBlock’s blocking rules or uninstall the app.
Why is the page blank instead of showing a message?
AppBlock uses a clean blank file to avoid distraction and reduce visual noise.